DDOS Mitigation
DDoS mitigation is a set of methods or tools for resisting or mitigating the impact of distributed denial-of-service (DDoS) attacks on networks attached to the Internet by protecting the target and relay networks. DDoS attacks are a continuous threat to businesses and companies by threatening service performance or to shut down a website entirely, even for a short period. So, explore this article and know more about DDoS mitigation.
WHAT IS DDOS MITIGATION
The term DDoS mitigation refers to the process of successfully protecting a target from a distributed denial of service (DDoS) attack.
A typical mitigation process can be generally defined by these four stages:
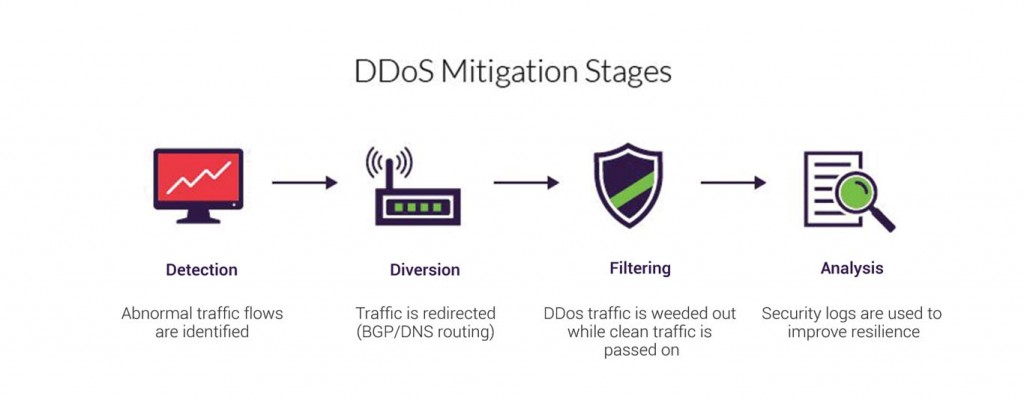
Detection: The identification of traffic flow aberrations that may signal the build-up of a DDoS attack. Efficiency is measured by the ability to recognize an attack as early as possible, with prompt detection is the ultimate goal.
Diversion: Traffic is redirected away from its target, either to be filtered or completely discarded.
Filtering: DDoS traffic is weeded out, usually by identifying patterns that instantly distinguish between legitimate traffic and malicious visitors. Responsiveness is a function of being able to block an attack without interfering with the user’s experience. The aim is the solution to be completely transparent to the site visitors.
Analysis: Security logs are studied to gather information about the attack, both to identify the offenders and to improve future resilience. The process of effectiveness relies on the existence of security logs that can offer granular visibility into the attack traffic.
CHOOSING A MITIGATION PROVIDER
Besides the method of traffic deviation, there are several other key aspects one must consider while choosing a mitigation provider. They are as follows:
NETWORK CAPACITY
Network capacity remains a great way of benchmarking a DDoS mitigation service. It is measured in Gbps (gigabits per second) or Tbps (terabits per second) and returns overall scalability available to the user during an attack.
Most of the cloud-based mitigation services offer multi-Tbps network capacity. On-premise DDoS mitigation appliances, on the other hand, are covered by default, both by the size of company’s network pipe and the internal hardware capacity.
PROCESSING CAPABILITIES
In addition to the capacity, consideration should also be given to the processing capabilities of the user’s mitigation solution. They are represented by redirecting the rates, measured in Mpps (millions of packets per second).
TIME TO MITIGATION
Once an attack has been detected, time to mitigation is critical. Most attacks can take down a target in a matter of minutes and the recovery process can take hours. The undesirable impact of such downtime can potentially be felt by the company for weeks and months ahead.
By providing pre-emptive detection, always-on solutions will have a distinct advantage. They offer an instant mitigation protecting the company from the first hail during any attack.
Not all the solutions offer a response level. That is why inquiring about time to mitigation should be on the user’s list when assessing a DDoS protection provider, in addition, while testing it during a service trial.

